At its heart, a GUID UUID generator is a tool that creates unique serial numbers for just about anything you can imagine in the digital world. The real magic is its ability to ensure that no two identifiers are ever the same, anywhere on the planet, even if they're generated completely offline. This frees developers from relying on a central server to hand out unique numbers and prevent duplicates.
What Are GUIDs and UUIDs
Picture a massive online store. You've got millions of products, customers, and orders flying around. How do you make sure every single one of these things has its own unique ID? What happens if two developers, working on different continents, accidentally give the same ID to a new product and a new customer? Chaos. The entire system could grind to a halt.
This is exactly the problem that GUID and UUID generators were designed to solve.
They produce a 128-bit number that, for all intents and purposes, is guaranteed to be unique. You can think of it as a digital fingerprint for a piece of data. This simple string of characters—a Globally Unique Identifier (GUID) or a Universally Unique Identifier (UUID)—is one of the unsung heroes of modern distributed systems, allowing them to grow without falling apart.
The GUID vs UUID Distinction
You'll often hear the terms GUID and UUID used interchangeably, and there's a good reason for that: they are functionally the same thing.
- UUID (Universally Unique Identifier) is the official standard, specified in a technical document called RFC 4122. It's the name the broader tech community uses.
- GUID (Globally Unique Identifier) is simply what Microsoft called its implementation of the UUID standard.
While there were some tiny differences in very early, non-standard versions from Microsoft, that's ancient history. Today, any GUID you create on a Windows machine is a standard UUID. So, in any modern context, you can treat the terms as synonyms. The core idea is the same: create a one-of-a-kind ID that will never clash with another.
Why Do We Need Them
The real power of a guid uuid generator is that it works without any central coordination. A developer in Tokyo and another in New York can both generate UUIDs for their parts of an application, confident that those IDs will never, ever conflict. This decentralized approach is absolutely critical for modern software.
It’s used everywhere for things like:
- Database Primary Keys: Giving every new record a unique ID without waiting for the database to assign the next number in a sequence.
- Transaction Tracking: Creating a unique, hard-to-guess reference for every API call, financial transaction, or important log entry.
- Session IDs: Securely managing user sessions across a whole farm of servers.
- System Integration: Making sure data stays clean when you're merging records from completely different systems.
For a quick example, take a look at a simple, browser-based generator that works entirely offline, which means your data stays completely private.
Tools like this one from Digital ToolPad show you just how fast and easy it is. A single click gives you a fresh, unique ID, and nothing ever leaves your computer. By letting developers create identifiers independently and offline, these generators are a cornerstone for building robust, scalable, and secure applications.
Choosing the Right UUID Version for Your Project
Not all UUIDs are created equal. They actually come in different "versions," and each one is designed for a specific job. Think of it like picking the right tool from a toolbox—you wouldn't use a sledgehammer to hang a picture frame, would you? The UUID version you choose really boils down to your project's needs for uniqueness, security, and predictability.
Getting this choice right is key. Using the proper settings in a guid uuid generator ensures you get the unique, secure, or predictable identifier you're actually expecting. Let's break down the most common versions you'll run into.
This diagram helps visualize how Microsoft's GUID fits into the broader UUID standard.
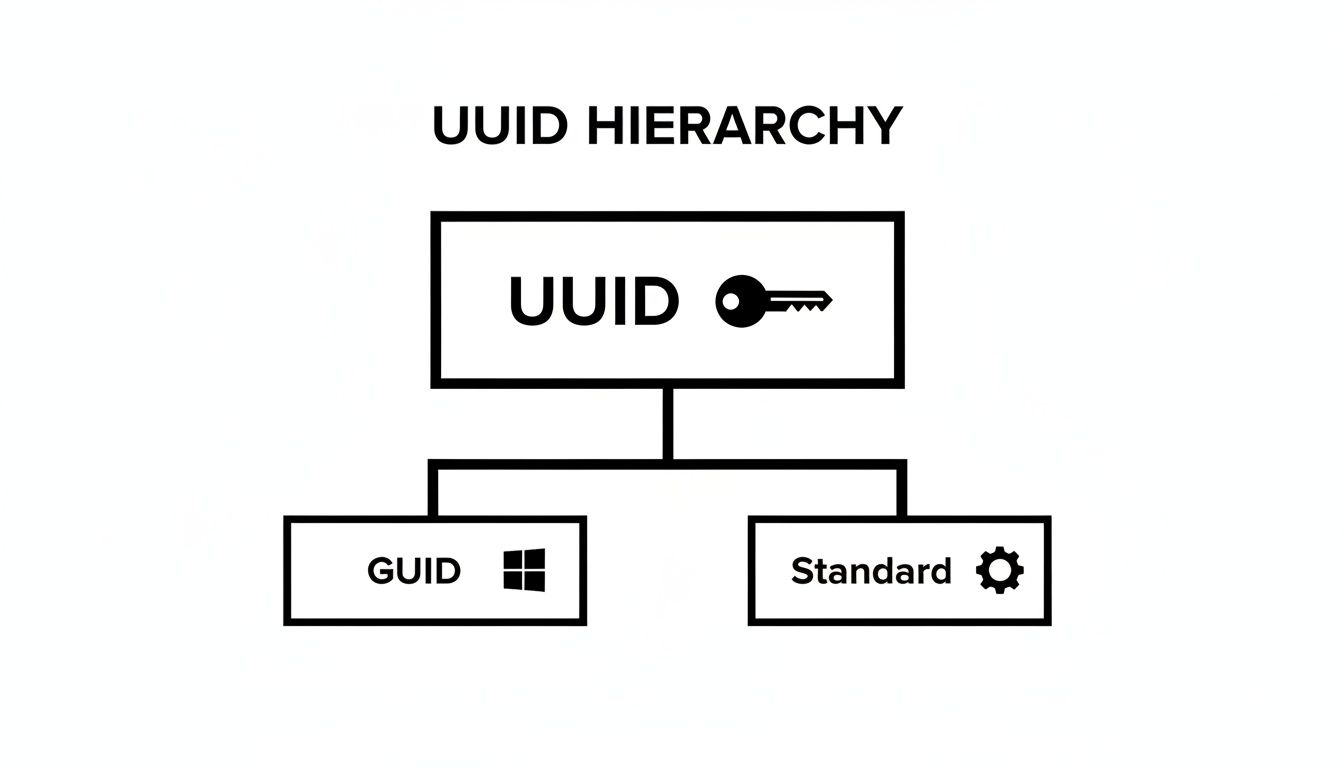
As you can see, while "GUID" is a term that originated with Microsoft, it's really just their implementation of the official UUID standard. For all practical purposes in modern development, they're the same thing.
Version 4: The Random Standard
UUIDv4 is the undisputed workhorse of the identifier world. It's by far the most widely used version today, and for good reason: it's built on pure, unpredictable randomness.
- How it works: It uses 122 bits of cryptographically secure random data to generate the ID.
- Best for: Pretty much any scenario where maximum unpredictability is what you need. Think API keys, session tokens, database primary keys, or any security identifier where the sequence is irrelevant.
Because it’s completely random, a Version 4 UUID reveals absolutely nothing about when or where it was created. This makes it a fantastic and secure choice for most applications.
Version 1: Time-Based Identifiers
A UUIDv1 is generated by combining a high-precision timestamp with the MAC address of the computer that created it. This structure gives it a unique characteristic: it's sortable by creation time.
That might sound useful, but it comes with a serious privacy trade-off. Exposing the MAC address and creation time can leak sensitive information about your infrastructure and exactly when certain events happened. Because of these privacy issues, Version 1 is rarely used for public-facing identifiers anymore.
Versions 3 and 5: Name-Based and Repeatable
What if you need to generate the exact same UUID for the exact same input, every single time? That’s where UUIDv3 and UUIDv5 come into play. They create a deterministic identifier from two inputs: a "namespace" and a "name" (like a URL or a username).
The key thing to remember is that these versions are not random at all. They are repeatable by design, which is perfect for tasks like de-duplicating records or creating stable identifiers for resources based on a URL.
The only real difference between them is the hashing algorithm they use to combine the inputs:
- Version 3: Uses the older and less secure MD5 algorithm.
- Version 5: Uses the much more secure SHA-1 algorithm.
For any new project, you should always choose Version 5 over Version 3. It’s simply the more secure and modern option. For a deeper dive, you can explore our guide to generating UUIDs online, which covers various creation methods.
Comparison of Common UUID Versions
To help you decide at a glance, this table breaks down the key differences between the most popular UUID versions you'll encounter.
| UUID Version | Generation Method | Uniqueness Source | Best For |
|---|---|---|---|
| Version 1 | Time + MAC Address | Timestamp and unique hardware | Time-series data where sorting is critical and privacy is not a concern. |
| Version 4 | Cryptographic Randomness | 122 bits of random data | Security tokens, API keys, database keys, and general-purpose unique IDs. |
| Version 5 | Name-Based (SHA-1) | A unique name within a namespace | Generating repeatable IDs from inputs like URLs, DNS entries, or user IDs. |
Ultimately, picking the right version is a strategic choice. If you need pure, unpredictable uniqueness with no strings attached, Version 4 is almost always your answer. If you need a consistent, repeatable identifier derived from a specific input, Version 5 is the secure and correct choice.
Why UUID Collisions Are Practically Impossible
If you've ever used a guid uuid generator, a nagging question probably crossed your mind: what if someone, somewhere else in the world, generates the exact same ID at the same time? It certainly feels like it should happen eventually.
But the reality is, the math behind UUIDs makes this scenario so wildly improbable that for all practical purposes, it's considered impossible. This is what makes them so powerful. It's the reason distributed systems can work without a central server handing out unique numbers—the math gives us all the confidence we need.
So, Just How Big is 128 Bits?
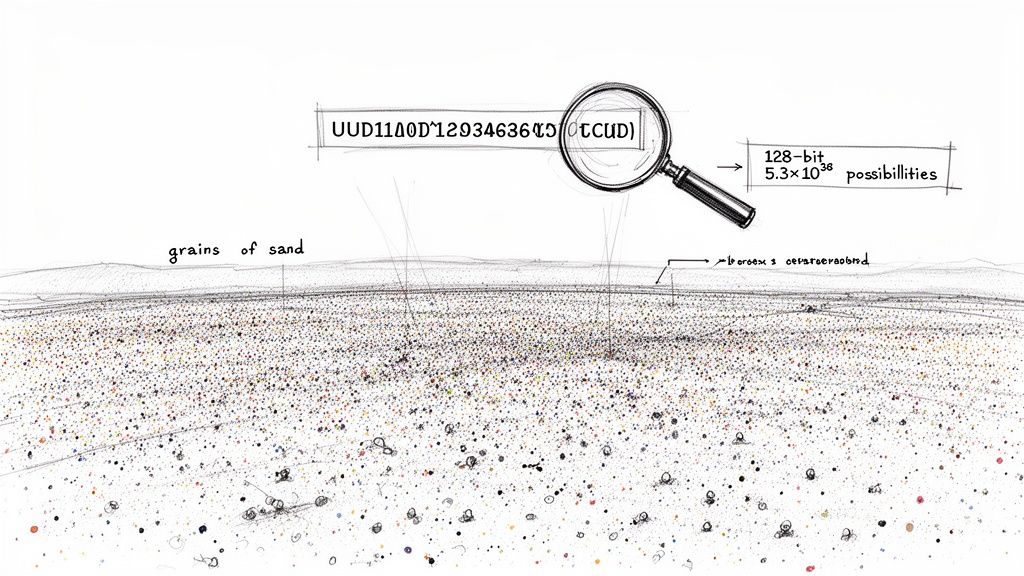
Let's get a feel for the numbers here. A 128-bit number offers a staggering 2¹²⁸ possible combinations. That works out to roughly 340 undecillion, which is a 340 followed by 36 zeros.
It's a number so large our brains can't really process it. So let's try an analogy.
Scientists estimate there are about 7.5 quintillion grains of sand on Earth. Imagine you could assign a unique UUID to every single one. After tagging every grain on every beach and desert, you would have barely made a dent in the total pool of available UUIDs. You could then do the same for billions of other Earth-like planets and still not run out. That's the scale we're talking about.
To put it another way, you're more likely to have a hardware failure corrupt a generated UUID than you are to have two separate systems randomly generate the same one. The probability is so low it effectively rounds down to zero.
This mathematical certainty is the bedrock of decentralized applications. It lets developers build massive, globally-scaled systems where any part can create its own identifiers without ever needing to check in with a central authority.
The Math Behind Version 4 Uniqueness
Let's zero in on Version 4 UUIDs, since they're the most common type and are based on randomness. A Version 4 UUID isn't 128 bits of pure randomness; 6 bits are used to denote the version and variant, leaving 122 bits for the random data.
This gives us 2¹²² unique possibilities, or about 5.3 undecillion. Even if you generated one billion UUIDs every single second, it would take you many lifetimes—longer than the current age of the universe, in fact—to have even a tiny chance of a collision. If you want to dive deeper into the technical details, you can explore the official UUID standards and their mathematical underpinnings.
So when someone asks, "Can a UUID collision actually happen?" The practical, real-world answer is a confident "no."
What Makes Collisions So Negligible?
The enormous number space is the main reason, but it's not the only one. The quality of the randomness used by the guid uuid generator is just as important.
Here are the key factors that make collisions a non-issue:
- Cryptographically Secure Randomness: Modern UUID libraries don’t just pull numbers out of a hat. They tap into high-quality, unpredictable entropy sources from the operating system, ensuring the output is truly chaotic and can't be guessed.
- Decentralized by Nature: Each ID is generated locally on a machine. There's no network call or central server, which means there are no bottlenecks or single points of failure that could compromise uniqueness.
- The "Birthday Problem" Isn't a Problem: You might have heard of the "Birthday Problem," a statistical concept showing you only need 23 people in a room to have a 50% chance of a shared birthday. With UUIDs, the "room" is so vast that you'd need to generate trillions of IDs before the probability of a collision even becomes worth thinking about.
In the end, UUIDs are a brilliant piece of engineering. They strike the perfect balance between an ironclad guarantee of uniqueness and the efficiency needed for modern software. This trust is what makes them an indispensable tool for building the robust, interconnected systems that run our world.
How to Generate UUIDs Securely and Offline
When you need a UUID, you want it to be secure, private, and available instantly. The absolute best way to tick all those boxes is to generate it offline, right on your own machine. This simple step cuts out network latency, gets rid of any reliance on third-party servers, and most importantly, keeps your data exactly where it belongs—with you.
For anyone in development or security, this isn't just a nice-to-have; it's a core security practice. Thinking about the security of your identifiers from the very beginning is a key part of the shift-left security approach, which is all about building security in, not bolting it on later. The good news is that generating UUIDs offline is incredibly easy, whether you use a browser-based tool or a few lines of code.
Using a Privacy-First Browser Generator
The fastest way to grab a UUID without touching a line of code is with a client-side guid uuid generator. These tools are built to run completely inside your web browser, tapping into its native cryptographic functions to produce secure IDs.
The biggest win here is that no data ever gets sent over the internet. This is a foundational feature for privacy-conscious toolkits like the offline UUID generator on Digital ToolPad. The whole operation happens locally on your computer, making it the perfect choice when you're working on confidential projects or handling sensitive information.
Here’s a look at what you can expect from a typical browser-based generator.
It’s as simple as it looks. You click a button, and a fresh, cryptographically random Version 4 UUID pops up, ready for you to copy and paste wherever you need it.
Programmatic Generation In Your Favorite Language
When you need to integrate UUIDs directly into your application, you're in luck. Every major programming language comes with built-in libraries that handle the job for you, securely and efficiently. Below are some quick, copy-and-paste examples for generating the industry-standard Version 4 UUID in JavaScript, Python, and Java.
Key Takeaway: Always stick to your language's standard library for generating UUIDs. These libraries are battled-tested, maintained by experts, and are designed to pull randomness from secure, OS-level sources. That's your guarantee for high-quality, unpredictable identifiers.
JavaScript (Node.js and Browser)
In any modern JavaScript environment, the crypto module is your go-to for anything requiring cryptographic strength. It offers a dead-simple method for creating a Version 4 UUID.
// Generates a secure Version 4 UUID const newUuid = crypto.randomUUID();
console.log(newUuid); // Example Output: 'f8c3de3d-1fea-4d7c-a8b0-29f63c4c3454'
That one line is all it takes. It’s completely safe for both backend Node.js applications and frontend browser code, as crypto.randomUUID() has become a standard feature across the board.
Python
Python makes UUID generation a breeze with its powerful uuid module, which is part of the standard library. The uuid4() function is what you'll use to create a random Version 4 UUID.
import uuid
Generates a random Version 4 UUID
new_uuid = uuid.uuid4()
print(new_uuid)
Example Output: 123e4567-e89b-12d3-a456-426614174000
The library is also flexible enough to handle other versions. For instance, you can easily create other types of UUIDs:
uuid.uuid1(): Generates a Version 1 (time-based) UUID.uuid.uuid5(uuid.NAMESPACE_DNS, 'example.com'): Creates a repeatable Version 5 (name-based) UUID from a given name and namespace.
Java
Java has had a robust UUID class in its core library for a long time. The static method randomUUID() is the standard for creating a secure Version 4 UUID.
import java.util.UUID;
public class UuidGenerator { public static void main(String[] args) { // Generates a random Version 4 UUID UUID newUuid = UUID.randomUUID();
System.out.println(newUuid.toString());
// Example Output: 7b5f7e7a-8f4f-4f1e-9a3d-8c4d1c4a1b2c
}
}
This method is thread-safe and hooks into a cryptographically strong random number generator, making it a reliable choice for any enterprise-level application. By using these standard functions, you’re ensuring your identifiers are not only unique but also created according to well-established security practices.
Using UUIDs in Enterprise Database Systems
When you move from writing code to designing system architecture, the choice of a primary key for your database becomes a major decision. It often boils down to a classic showdown: the simple, fast, auto-incrementing integer versus the scalable, secure UUID. There’s no single right answer, just a series of important trade-offs.
The first thing you’ll notice is the difference in size. A typical integer ID takes up just 4 bytes. A UUID, on the other hand, stored as a standard string, eats up 36 bytes. For a small table, who cares? But when you're dealing with enterprise systems that handle billions of records, that difference quickly balloons into terabytes of extra storage and a heavier memory footprint for your indexes.
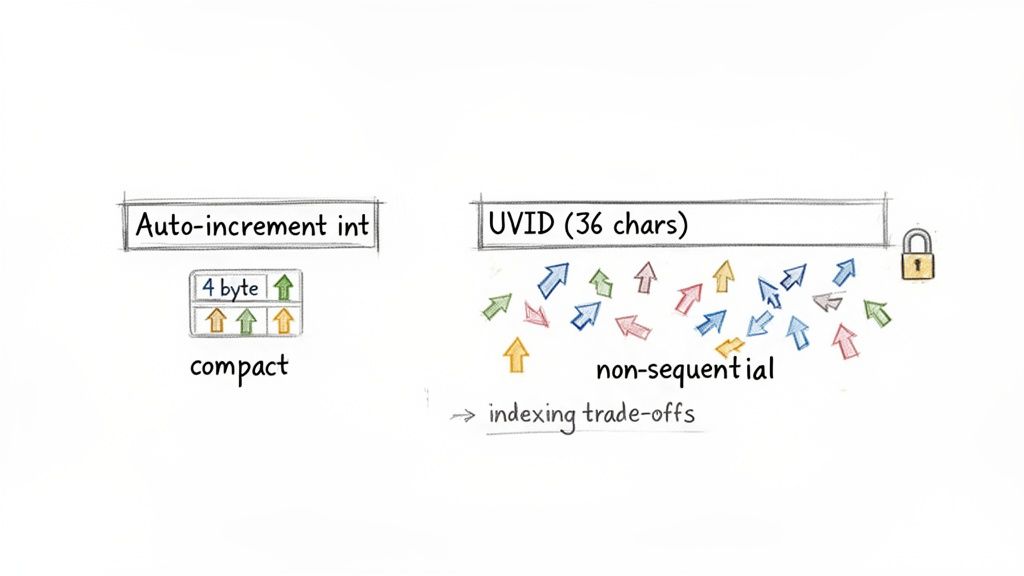
For a large organization, this isn't just about buying more hard drives. It directly affects hardware costs, how much memory you need for caching, and even how fast your queries run. Deciding to use UUIDs means you've weighed these costs and decided their benefits in a distributed environment are worth it.
The Security Advantage of Non-Sequential IDs
Performance debates aside, UUIDs bring a security benefit to the table that's hard to ignore in modern applications. Auto-incrementing IDs are predictable. It's just simple math. If a customer sees their order is number 1005, they know for a fact that order 1004 exists. What’s stopping them from trying to poke around and view it?
This predictability is also a business intelligence leak waiting to happen. A competitor could easily create an account, look at their new user ID, and get a shockingly accurate estimate of your total user base or how many people sign up each day. Randomly generated UUIDs shut this down completely.
A Version 4 UUID like
f47ac10b-58cc-4372-a567-0e02b2c3d479tells you absolutely nothing. You can't guess the next ID or the previous one, which is a simple and effective way to stop enumeration attacks and keep your business metrics private.
This is a fundamental piece of building a secure system from the ground up. To get it right, your approach to identifiers should align with broader Top Software Engineering Best Practices that bake security in from day one.
Mitigating Performance Hits in Large Databases
So, what about that performance hit? The biggest headache with random UUIDs (like Version 4) comes from database indexing. Since each new ID is random, it gets inserted at a random spot in the index. This causes constant shuffling, page splits, and fragmentation over time. It's far less efficient than just tacking a new record onto the end of the index, which is what happens with a nice, orderly sequential integer.
Luckily, engineers have come up with some clever ways to get the best of both worlds.
- Store UUIDs as Binary: This is the easiest win. Instead of a 36-character string, you can store the UUID in its native 16-byte binary form. This alone cuts storage by more than half and makes indexing much faster. Most modern databases, like Oracle or SQL Server, have dedicated
UUIDorRAW(16)data types just for this. - Use Time-Ordered UUIDs (v6, v7): This is where things get really interesting. Newer UUID versions, especially the up-and-coming Version 7, are designed to be sortable. They cleverly combine a timestamp at the beginning with random data at the end. This ensures new IDs are always sequentially greater than old ones, allowing the database to append them neatly to the index. No more fragmentation!
This hybrid approach gives you the global uniqueness of a UUID and the database-friendly, sequential nature of an auto-incrementing key. It’s a powerful solution for systems that need to handle a high volume of writes.
At the end of the day, using UUIDs in a large-scale database is a serious architectural decision. They add some complexity around storage and indexing, but their advantages for distributed systems and security are often non-negotiable. By understanding the trade-offs and using smart strategies to manage performance, you can build systems that are scalable, resilient, and secure. Building secure systems is a deep topic, and you can learn more in our guide on software development security best practices.
A Few Lingering Questions About UUIDs
Even after you've got the basics down, a few practical questions always seem to pop up when you start implementing UUIDs in a real project. This section is here to tackle those common head-scratchers head-on, giving you clear, straightforward answers. Think of it as a final sanity check before you dive in.
Can a UUID Generator Actually Create a Duplicate?
The short answer? For all practical purposes, no.
While it's theoretically possible, the probability is so mind-bogglingly small it's not worth losing sleep over. For a standard Version 4 UUID, the chance of a random collision is about 1 in 5.3 undecillion. That's a 5 with 36 zeros after it.
To give you some perspective, you'd have to generate a billion UUIDs every second for well over a hundred years to even have a tiny chance of seeing a duplicate. This is why they're the go-to for massive, decentralized systems where you can't have a central authority handing out numbers. The randomness comes from high-quality sources, making the risk of a duplicate a purely academic conversation, not a real-world problem.
What's the Real Difference Between GUID and UUID?
In modern tech, there's no real difference. You can think of them as two names for the same thing.
UUID (Universally Unique Identifier) is the official, open-standard name defined by the IETF in RFC 4122. GUID (Globally Unique Identifier) is just what Microsoft called its own implementation of that very same standard.
Back in the early days of computing, there were some minor, non-standard quirks in Microsoft's implementation, but that's ancient history now. Any GUID you generate today on a modern Windows system is a perfectly valid, standards-compliant UUID.
So, when you're in the trenches coding, feel free to use the terms interchangeably. They both point to the same 128-bit identifier. Which term you use usually just depends on whether you're working in a .NET or a Java ecosystem.
When Should I Use UUIDs Instead of Integers for Primary Keys?
Ah, the classic database debate. Choosing between a UUID and a good old-fashioned auto-incrementing integer for a primary key really comes down to your system's design and what you're trying to achieve. It's a trade-off.
You should definitely reach for UUIDs in these situations:
- Distributed Systems: This is the killer use case. If you have multiple services or database shards that need to create IDs independently without talking to each other, UUIDs are your best friend.
- Offline-First Apps: When a user's device needs to create new records while offline, UUIDs ensure that when they eventually sync, there won't be any ID collisions.
- Security: UUIDs are not guessable. If you use sequential integers for user IDs or order numbers (
/users/101,/users/102), you're making it easy for someone to guess how many users or orders you have. UUIDs hide that information.
On the other hand, stick with simple auto-incrementing integers when:
- You Have a Monolith: If your application uses a single database, a central counter is simple, fast, and perfectly fine.
- Performance is Everything: Integers are much smaller (usually 4 or 8 bytes vs. 16 for a UUID), which means your database indexes are smaller and your queries can be a touch faster.
The decision boils down to this: do your needs for scalability, offline generation, and security outweigh the small hit you'll take on storage and performance?
How Do I Properly Validate a UUID String?
Validating a UUID is a crucial step to protect your application's data integrity. Letting a badly formatted ID slip into your system can cause all sorts of headaches, from weird bugs to database errors.
The best way to check a UUID is by using a regular expression (regex) or a built-in function provided by your programming language's standard library. A valid UUID has a very specific 8-4-4-4-12 structure of hexadecimal characters, like this: 123e4567-e89b-12d3-a456-426614174000.
Here's how you can handle it in a few popular languages:
- Python: The
uuidlibrary makes this easy. Just try to create a UUID object from the string—if it’s invalid, the code will raise aValueError. - JavaScript: A simple regex pattern is the most common way to test if a string matches the required format.
- Java: Much like Python, the
UUID.fromString()method will throw anIllegalArgumentExceptionif you feed it a bad string.
Always make it a rule to validate any UUID you get from an external source or user input before you save or use it. It's a simple, defensive check that keeps your system robust and reliable.
For all your development needs, from generating UUIDs to converting data formats, Digital ToolPad provides a suite of powerful, privacy-first tools that run entirely in your browser. Experience the speed and security of 100% offline utilities. Explore the full toolkit at https://www.digitaltoolpad.com.
