End-to-end encryption is a powerful way to keep digital conversations private. At its core, it's a security method designed to stop anyone—and we mean anyone—from peeking at your data as it travels from one device to another.
With end-to-end encryption (E2EE), only you and the person you're communicating with can read what's sent. Nobody in the middle can decipher it. Not the app's creator, not your internet provider, and not even government agencies with a warrant. Think of it as the digital version of a sealed letter that can only be opened by its intended recipient.
Decoding Digital Privacy
Let's use an analogy. Imagine you need to send a valuable package across the country. With typical security, the courier company might lock your package inside a secure truck. That's good, but they still have the key. If they wanted to, or if someone forced them to, they could open that truck and see what's inside. This is how most standard encryption works—it protects data on its journey, but the company providing the service often holds the keys to unlock it on their servers.
End-to-end encryption changes the game entirely. It’s like you place your item in a special lockbox, and only you and your friend have the key. You snap it shut before it even leaves your hands, and it stays locked until the moment it arrives. The courier can handle the box, track it, and deliver it, but they have absolutely no way to open it.
This simple but profound shift creates a truly private communication channel. The "ends" of the conversation—your device and the recipient's—are the only places with the cryptographic keys needed to scramble and unscramble the information.
Core Principles of E2EE
This level of security is built on a few foundational ideas that work in concert to protect your information from prying eyes:
- Confidentiality: The main event. It ensures the content of your message is complete gibberish to anyone except the intended users.
- Integrity: Guarantees that the message you receive is the exact same one that was sent, with no tampering or alterations along the way.
- Authentication: Helps prove you’re talking to the right person, preventing imposters from jumping into your conversation.
This robust trifecta is why E2EE is considered the gold standard for private communication today. It's the technology that powers apps like Signal and WhatsApp to protect the privacy of billions of conversations every single day.
End-to-End Encryption vs Standard Encryption
To really get why E2EE is so important, it helps to compare it directly with the more common encryption you encounter every day, like when you visit a secure website using HTTPS. They sound similar, but the difference in who can access your data is massive.
The table below breaks down the fundamental differences between E2EE and other encryption models.
| Feature | End-to-End Encryption (E2EE) | Standard Encryption (In-Transit/At-Rest) |
|---|---|---|
| Data Accessibility | Only the sender and recipient can access the unencrypted data. | The service provider (e.g., email host, cloud service) can access the data. |
| Encryption Point | Data is encrypted on the sender's device before being sent. | Data is encrypted between your device and the server, then often re-encrypted at rest. |
| Weakest Link | Compromise of the end-user devices (endpoints). | Compromise of the service provider's servers. |
| Example Use Case | Private messaging apps (Signal), secure file sharing. | Secure websites (HTTPS), encrypted cloud storage (server-side). |
As you can see, the key distinction lies in where the data is protected and who holds the keys. While standard encryption is essential for protecting data from outside attackers, E2EE goes a step further by also protecting it from the service provider itself.
How End-to-End Encryption Actually Works
To really get what makes end-to-end encryption so secure, we need to pop the hood and look at the cryptographic engine that drives it. At its heart, E2EE is a clever tag team of two different encryption types, each with a very specific job in building a truly private line of communication.
The whole dance starts with something called asymmetric cryptography, which you might also hear called public-key cryptography. Think of it as the secret handshake that lets two people who've never met set up a secure channel right in the middle of an insecure place, like the open internet.
The Digital Lock and Key Analogy
It’s easiest to picture this as a personal lockbox system for every user. Each person gets two keys that are mathematically tied together: a public key and a private key.
- Public Key: This is like a mail slot on your front door. You can give out its location to anyone and everyone. It’s public knowledge, and anyone can use it to drop a message into your lockbox.
- Private Key: This is the only physical key that can open that lockbox. You keep it on you at all times and never, ever share it.
So, when someone wants to send you a secure message, they use your public key to "lock" it. Once that message is sealed, the only thing on earth that can unlock it is your corresponding private key. This one-way street is the genius of asymmetric encryption, but it's a bit slow and heavy for a fast-paced chat.
Building a Shared Secret
If asymmetric encryption is too clunky for entire conversations, what's the alternative? This is where a key exchange comes in, with one of the most common methods being the Diffie-Hellman key exchange.
It's a brilliant mathematical trick that lets two people agree on a shared secret key over a public channel without ever actually sending the key itself. It’s like two artists agreeing on a secret paint color by mixing their own secret colors with a common base color out in the open. Even if someone sees the process, they can't figure out the final secret shade.
Once that shared secret is established, the conversation can switch gears to a much faster encryption method. This flowchart gives you a bird's-eye view of how a message stays locked down from start to finish.
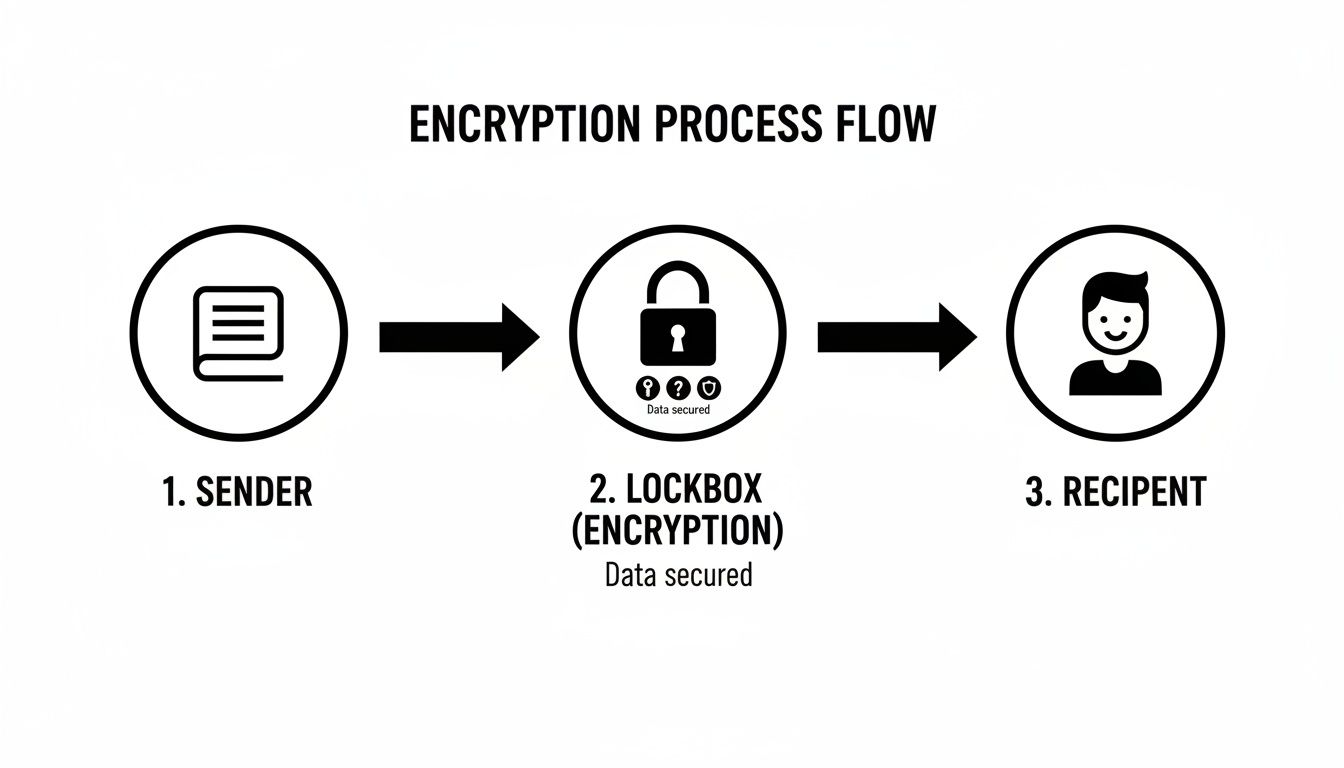
With the shared key in hand, the system moves on to symmetric encryption for the rest of the conversation. Here, the same key both locks and unlocks the messages. It's lightning-fast and efficient, perfect for the back-and-forth of a real-time chat. If you want to dive deeper into the nuts and bolts, our guide on how to https://www.DigitalToolpad.com/blog/decrypt-encrypted-text is a great next step.
The Signal Protocol and Forward Secrecy
Modern E2EE has come a long way. A major breakthrough was Off-the-Record (OTR) messaging back in 2004, which introduced a crucial concept called perfect forward secrecy. This is a powerful guarantee: even if an attacker steals your current keys, they still can't go back and decrypt your past messages.
Today, the Signal Protocol is the undisputed gold standard in secure messaging. It’s the engine inside apps like Signal, WhatsApp, and even Google Messages. It takes forward secrecy to a whole new level with an algorithm called the Double Ratchet.
The Double Ratchet algorithm is like a key-making machine that’s always running. It generates a brand-new, temporary encryption key for every single message you send, making each one a self-contained secret.
This constant key rotation is what makes it so robust. Compromising one key for one message tells an attacker absolutely nothing about the messages that came before or the ones that will come after. For a complete picture of online security, understanding TLS encryption is also key, as it's the protocol that protects most of your other web traffic while it's in transit.
E2EE in the Wild Real-World Examples
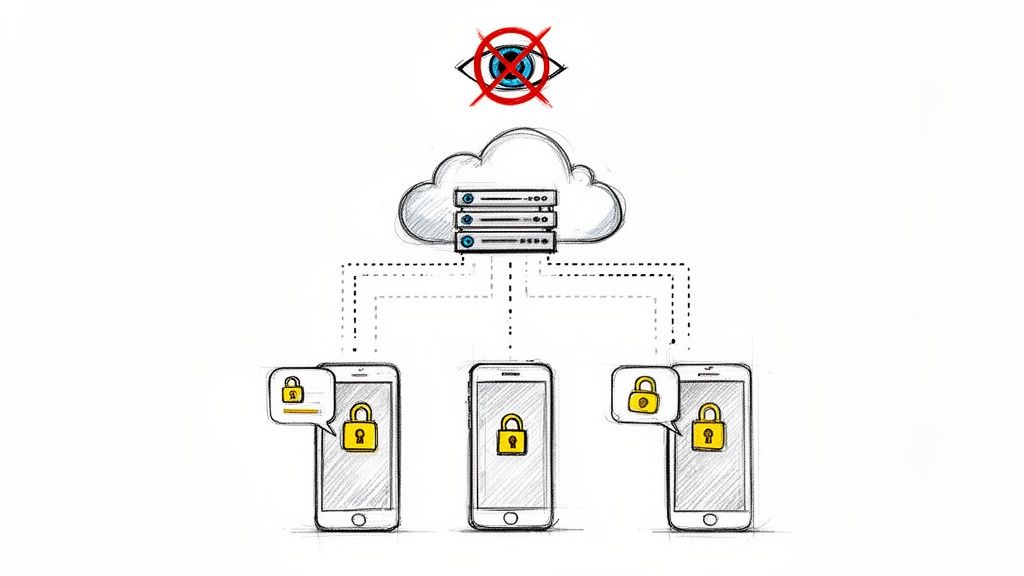
Theory is one thing, but seeing end-to-end encryption in action is what makes it all click. You actually use it every single day, probably without even thinking about it, especially in the messaging apps that have become a core part of our lives.
Take apps like Signal and WhatsApp. They've made E2EE the default for billions of people. When you fire off a message, send a photo, or start a call, that conversation is scrambled the instant it leaves your phone and only unscrambled when it arrives on your friend's device. It creates a truly private digital space where only you and the recipient can ever see the content.
The Catalysts for Widespread Adoption
This push for default E2EE didn't just appear out of nowhere. The Edward Snowden disclosures back in 2013 were a massive wake-up call. They peeled back the curtain on global surveillance programs and proved that even established encryption methods could be compromised.
This sparked a huge demand from both the public and developers for communication that was provably secure. E2EE went from a niche tool for security experts to a feature people started to expect. Before the revelations, a tiny slice of web traffic was encrypted. By 2018, that number had skyrocketed to 70% for HTTPS alone, which tells you everything about the shift in priorities. You can learn more about the historical context of cryptography and how it has evolved to meet these new challenges.
This new privacy-conscious mindset fueled the growth of apps built on security. Signal, which launched in 2014, quickly became the gold standard for its strong, open-source protocol. Then, in 2016, WhatsApp rolled out E2EE to its two billion users, securing an estimated 60 billion messages every single day and completely changing the game for private communication.
A Common Point of Confusion TLS vs E2EE
Here’s a critical distinction that trips up a lot of people, even developers. The encryption that secures your web browsing—the little padlock icon—is not the same as true end-to-end encryption. That padlock signifies TLS (Transport Layer Security), the protocol that puts the "S" in "HTTPS."
TLS is absolutely essential. It encrypts the data flowing between your browser and a website's server, stopping anyone on the network from snooping on your connection.
But here’s the catch: TLS only protects data in transit. The moment your information hits the server, it’s decrypted. This means the service provider—your email host, cloud storage company, or social media platform—can read it. They often need to for the service to work, but it creates a completely different privacy model.
End-to-end encryption protects your data from everyone, including the service provider. TLS protects your data from outsiders but gives the service provider full access.
This is arguably the most important thing to understand when you’re evaluating an application's security promises. The server is always a potential point of failure, whether from a hacker, a malicious insider, or a government subpoena. E2EE takes the server out of the equation as a weak link for your content.
Data Accessibility E2EE vs TLS
To make this crystal clear, let's break down who can actually read your unencrypted data in each model. This table really highlights why E2EE offers a much stronger privacy guarantee for sensitive communications.
| Access Point | End-to-End Encryption | TLS (HTTPS) |
|---|---|---|
| Sender | ✅ Can access data | ✅ Can access data |
| Recipient | ✅ Can access data | ✅ Can access data |
| Service Provider | ❌ Cannot access data | ✅ Can access data |
| Hackers on the Network | ❌ Cannot access data | ❌ Cannot access data |
| Government with a Warrant (to the provider) | ❌ Cannot access data | ✅ Can access data |
As you can see, with TLS, the service provider holds the keys to your plaintext data. With E2EE, that power stays exactly where it belongs: with the users at the "ends" of the conversation.
Where E2EE Falls Short: Critical Limitations
End-to-end encryption is a powerhouse for privacy, but it's not a silver bullet. Thinking of it as an impenetrable shield against every possible threat is a common mistake. To build genuinely secure software, you have to understand where its protection ends. E2EE is brilliant at protecting data in transit, but it can't solve every security problem on its own. It's one critical layer, but not the only one you'll need.
The biggest blind spot for E2EE has nothing to do with the strength of its cryptography. The real achilles heel is the endpoints—the very devices where your messages are encrypted and decrypted. If a device at either end of the conversation is compromised, all bets are off.
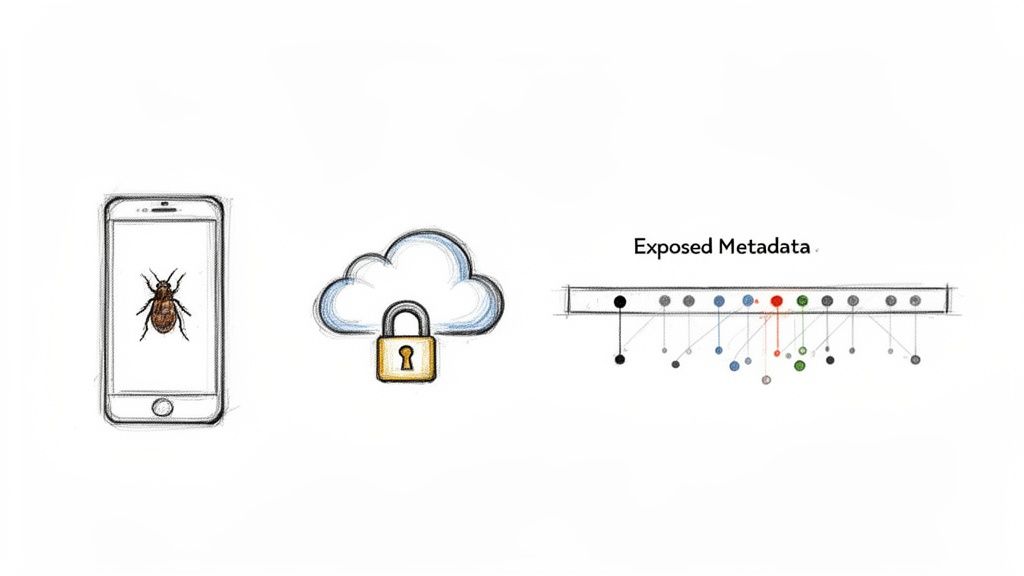
The Endpoint Vulnerability
I like to think of E2EE as an armored truck carrying a precious diamond. The truck is built like a fortress, nearly impossible to breach while it's on the road. But what happens if a thief is already inside the bank when the diamond is being loaded? Or if they're waiting inside the destination vault? Suddenly, the truck's armor doesn't matter much.
That's the endpoint problem in a nutshell. Any threat that compromises the device itself can simply grab the data before it gets encrypted or after it's been decrypted.
- Malware and Spyware: Malicious software running on a phone or computer can read messages right as they're being typed or displayed, completely sidestepping the encryption.
- Keyloggers: These nasty little tools record every keystroke, capturing the raw, unencrypted text of a message before it's even sent.
- Screen Scraping: An attacker could take screenshots of your conversations, making the encryption totally irrelevant.
End-to-end encryption secures the journey, not the origin or the destination. Once data is decrypted on a device, its security depends entirely on the integrity of that device.
The Problem of Metadata Leakage
Another major limitation is metadata. E2EE does a fantastic job of hiding the content of your communication—the "what." But it often leaves the context—the "who," "when," and "where"—exposed. This is the metadata, and service providers can almost always see it. And it can reveal a shocking amount about you.
For example, a messaging service might not know what you said, but they probably know:
- Who you're talking to.
- The exact time and date of your messages.
- How often and for how long you communicate.
- Your physical location when you sent the messages.
This metadata can be pieced together to build a detailed profile of your relationships, your daily habits, and your movements. For people in sensitive roles like journalists, activists, or whistleblowers, that kind of information can be just as dangerous as the content of the messages themselves.
Unencrypted Backups and Other Weak Points
A surprisingly common vulnerability that completely undermines E2EE is unencrypted backups. For convenience, many apps offer to back up your chat history to the cloud so you can restore it on a new device. The problem is, if those backups aren't also end-to-end encrypted, you've just created a massive security hole.
Think about it. If your E2EE messages are saved to a cloud service without that same level of protection, the cloud provider can read your entire conversation history. So can anyone who gets access to their servers, including law enforcement with a warrant. It's a backdoor that undoes all the hard work of the encryption in the first place.
And let's not forget the ongoing "crypto wars." Governments and agencies constantly push for lawful access and backdoors that would weaken encryption for everyone. Building a truly resilient system means layering your defenses. Our guide on software development security best practices dives much deeper into how you can create these crucial defense-in-depth strategies.
The Next Frontier: E2EE in a Post-Quantum World
The end-to-end encryption we rely on every day is incredibly robust. It’s built on mathematical puzzles so difficult that even the world's fastest supercomputers would take an eternity to solve them. But a new kind of computer is on the horizon—a quantum computer—and it doesn't play by the old rules.
These machines are being built to solve the exact kinds of problems that make our current encryption, like RSA and Elliptic Curve Cryptography, so secure. This isn't some far-off sci-fi concept; it's a fundamental challenge to our digital privacy, and we need to start preparing for it now. The very future of what is end-to-end encryption hinges on our ability to stay one step ahead.
The Threat of Shor's Algorithm
The main danger has a name: Shor's algorithm. Dreamed up back in 1994, it’s a blueprint showing how a powerful quantum computer could factor huge numbers at speeds a normal computer could only dream of.
Why does that matter? Because the security of our most common encryption methods depends on that exact task being impossibly hard. A quantum computer running Shor's algorithm could shatter the digital "lock and key" system we use for everything, making much of today's E2EE useless. It wouldn't just be cracking a single message—it would be like discovering a master key that opens every digital lock in the world.
This looming threat is often called the "quantum apocalypse" for cryptography. Attackers could be collecting our encrypted data right now, storing it, and waiting for the day when quantum computers are strong enough to break it wide open.
The Rise of Post-Quantum Cryptography
Fortunately, cryptographers haven't been sitting on their hands. For years, the global cybersecurity community has been developing a solution: Post-Quantum Cryptography (PQC). This is a whole new class of cryptographic algorithms built to withstand attacks from both classical and quantum computers.
Instead of relying on problems that Shor's algorithm can solve, these new methods are based on different, much harder mathematical foundations. The race to standardize these new defenses is already in its final stretch. The U.S. National Institute of Standards and Technology (NIST) has been spearheading a global, multi-year competition to vet and approve the best PQC algorithms.
This transition isn't just theoretical; it's happening. On August 13, 2024, NIST finalized three major post-quantum standards—FIPS 203 (ML-KEM), 204 (ML-DSA), and 205 (SLH-DSA). These are our first lines of defense against Shor's algorithm, which some estimates suggest could crack 2048-bit RSA with just 20 million qubits as early as 2030. Recognizing the urgency, the U.S. has already passed legislation like the Quantum Computing Cybersecurity Preparedness Act to accelerate the move to quantum-safe systems. You can discover more insights about the evolving history of encryption and these groundbreaking standards.
Preparing for the Future with Crypto-Agility
So, what does this mean for developers and companies building secure products? The keyword is crypto-agility.
This is the principle of designing systems so that you can swap out cryptographic algorithms without having to rebuild everything from scratch. Instead of hard-coding one specific encryption method, an agile system is flexible. As new standards like PQC are finalized and rolled out, your software can be updated easily. It’s about building for change, ensuring that as threats evolve, our security can evolve right alongside them to keep our data safe for decades to come.
The Local-First Approach: Privacy by Default
So far, we've focused on the best ways to protect data when it travels to a server. But what if we ask a more fundamental question: what if you never sent it in the first place? This is the core idea behind local-first architecture, an approach that takes the principles of end-to-end encryption to their logical conclusion. It redefines privacy by keeping your data on your device. Period.
Tools built this way operate entirely within your browser or on your machine. By their very design, they eliminate entire classes of risk that even the strongest server-based E2EE models have to grapple with. This architecture essentially creates a personal data fortress, giving you complete and total control.
Eliminating the Server as a Risk
The local-first model is disarmingly simple, yet incredibly powerful. When all data processing happens on the client side—your computer—there is no central server to attack, subpoena, or breach. This move immediately neutralizes several persistent threats that plague online services.
- No Server Breaches: If there's no server holding a trove of user data, it can't be stolen in a breach. This is a massive security upgrade, especially when you consider how often even major tech companies suffer from data leaks.
- No Metadata Collection: Since no information is transmitted, there's simply no metadata for a service provider to collect about when you use a tool, how you use it, or who you're connected to.
- Immunity to Lawful Access: Government requests or subpoenas for user data become irrelevant. The company literally has nothing to hand over, because it never had your data to begin with.
By taking the server completely out of the data-handling equation, local-first applications deliver privacy by default, not as an afterthought or an added feature. The most secure data is the data that never leaves your control.
Embracing this model is all about prioritizing user control, which is really a cornerstone of modern security thinking. For a deeper dive, you can explore the broader concept of privacy and why it's so critical in software design today.
Tangible Benefits Beyond Security
This isn't just a theoretical security exercise; the local-first model delivers practical advantages that you can feel immediately. Processing data locally unlocks a level of performance and reliability that cloud-dependent services often can't match.
For starters, you get zero network latency. Every action is instantaneous because there are no round-trips to a distant server and back. This makes tools feel incredibly snappy and responsive, which is a huge win for the user experience.
These tools also offer complete offline functionality. You can keep working without an internet connection, whether you're on a plane, in a remote area, or just dealing with a spotty network. The application is always available because it lives right there on your device. For developers building something like a QR code generator, this means their tool is always dependable. You can see exactly how a local-first QR code generator delivers on these benefits.
Finally, a local-first architecture dramatically simplifies compliance with tough privacy regulations like GDPR and CCPA. When you don't collect or process personal data on servers, the burden of proving compliance gets a whole lot lighter. It's a powerful, modern alternative that gives developers a clear path toward building maximum security and earning user trust.
Frequently Asked Questions
Even after getting the hang of end-to-end encryption, a few practical questions almost always pop up. Let's tackle some of the most common ones to clarify E2EE's real-world strengths and where its limits truly lie.
Is E2EE Completely Unbreakable?
No encryption is "unbreakable" in the absolute sense, but breaking the math behind modern E2EE with current technology is practically impossible. The real vulnerabilities aren't in the cryptography itself.
The weak points almost always show up elsewhere:
- Endpoint Compromise: If your device gets malware, an attacker can simply read your messages before they're encrypted or right after they're decrypted. The encryption doesn't matter if the endpoint isn't secure.
- Insecure Backups: Backing up your supposedly secure messages to a cloud service that doesn't also use E2EE is like locking your front door but leaving a key under the mat. It creates a massive backdoor.
- Metadata Analysis: While the message content is hidden, information about the message—who you're talking to, when, and how often—can still be exposed and analyzed.
Looking ahead, the rise of quantum computing does pose a theoretical threat to current standards, but this is a challenge the entire field is actively working on with Post-Quantum Cryptography (PQC).
Can Governments Force Companies to Bypass E2EE?
This is the million-dollar question at the heart of the "crypto wars." Governments frequently try to force tech companies to build backdoors or special access points into encrypted systems for law enforcement purposes.
With true end-to-end encryption, however, this is a technical non-starter. The service provider simply doesn't have the decryption keys, so there's nothing for them to hand over. To comply with such an order, a company would have to deliberately re-engineer its entire system to break the security model for all its users. This is precisely the fight companies like Apple have publicly waged, arguing it would undermine user privacy on a global scale.
The core principle of a "zero-knowledge" architecture means the platform cannot read user data. This makes forced access a technical impossibility, not just a policy choice.
What Is the Difference Between E2EE and a VPN?
They solve different problems, but they work great together. Think of it this way: end-to-end encryption protects the letter you're sending. It ensures that only the intended recipient can read the content inside the envelope.
A VPN (Virtual Private Network), on the other hand, protects the mail truck carrying your letter. It creates a secure, private tunnel for your entire internet connection, hiding your location (IP address) and preventing your internet provider from snooping on your activity. The VPN provider itself could, in theory, see your traffic, which is why choosing a trustworthy one is crucial. Using both gives you layers of security—one for your specific message, and one for your entire connection.
For developers and teams who demand absolute data privacy and control, Digital ToolPad offers a suite of powerful utilities that run 100% on your device. Eliminate server risk and ensure zero data exposure with our local-first tools. https://www.digitaltoolpad.com
